- Part 1: Complement your VDI environment with NSX
- Part 2: Complement your VDI environment with NSX: dFW
- Part 3: Complement your VDI environment with NSX: IDFW
- Part 4: Complement your VDI environment with NSX: Introspection Services
- Part 5: Complement your VDI environment with NSX: IDS/IPS
- Part 6: Complement your VDI environment with NSX: Advanced Load Balancer
Before I start. Shout out to Bilal Ahmed, a fellow vMusketeer who helped me with this post.
In this part of the series, we will look into IDFW (Identity Firewalling). IDFW is becoming an increasingly popular feature in VDI and RDSH environments. It allows security constructs to be applied to AD (Active Directory) groups, rather than the IP addresses. This promotes ease of mobility and reduction of operational effort on Day 2. This also helps security and compliance meet their goals in an ever-changing (COVID19) world.
Identity Firewall Concepts.
The IDFW functionality peers the NSX Managers with an authentication system, most commonly AD (or LDAP). It then allows the NSX administrators or security administrators to create NSX groups, based on AD groups. Subsequently, you can apply these dynamic groups to the dFW rules for a secure yet dynamic environment.
An example of this would be Jane in accounts. Jane logs into her VDI and using the power of NSX, dFW rules are pushed to the VM NIC permitting and/or denying access to specific accounts applications or areas of the network. If Jane was to move departments, say to finance, then typically Jane would have her VDI moved to another network, or be assigned a new VDI which is restricted based on her new requirements. Not when using NSX! The Network operational task is removed! When Jane is moved from AD group “accounts” to AD group “finance”, NSX realizes this and on Jane’s next login, that same VDI gets a fresh set of finance-related rules.
Links to Documentation
There is some great VMware documentation on IDFW and if you are interested in deploying IDFW, definitely check it out.
Enabling the Identity Firewall.
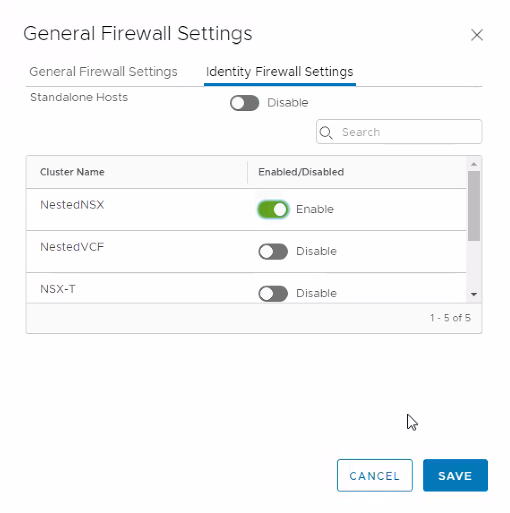
First of all, you need to enable the IDFW feature on the VDI cluster. This can be done by following the below procedure:
Select Security > Distributed Firewall.
In the right corner, click Actions > General Settings.
Click Identity Firewall Settings.
Toggle the status button to enable IDFW on the VDI cluster.
N.B. You may need to enable the IDFW feature in the General Firewall Settings.
Click Save
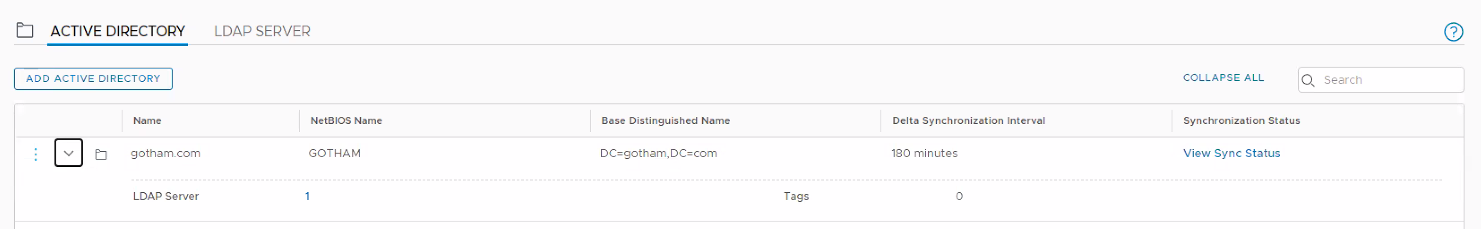
Once you have enabled IDFW on the cluster, you’ll need to link the NSX Manager to the AD server. This can be done by following the below procedure:
Navigate to System > Identity Firewall AD > Active Directory.
Click Add Active Directory.
Enter the name of the active directory.
Enter the NetBios Name and Base Distinguished Name.
Create an LDAP Server.
Click Save.
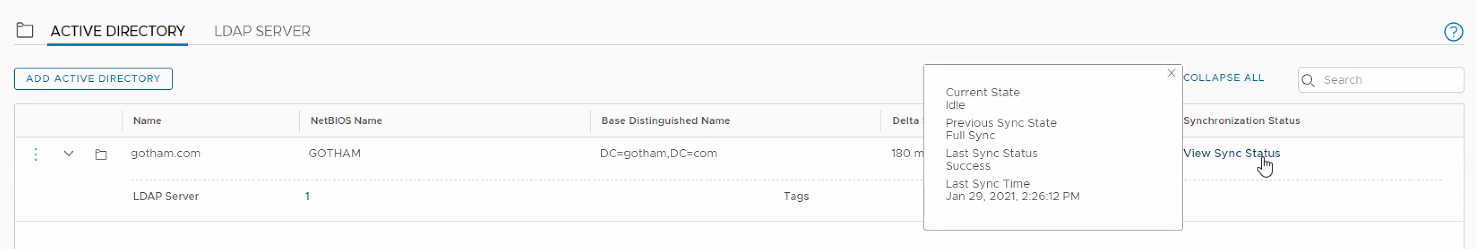
Finally, sync the newly configured AD server groups to the NSX Manager. This can be done by following the below procedure:
Navigate to System > Identity Firewall AD > Active Directory.
Click the three-button menu icon next to the Active Directory that you want to synchronize and select Sync All.
Wait for the synchronization to complete.
Adding Groups
Now that the NSX Manager has been synced with the AD Server. I can create groups based on AD variables.
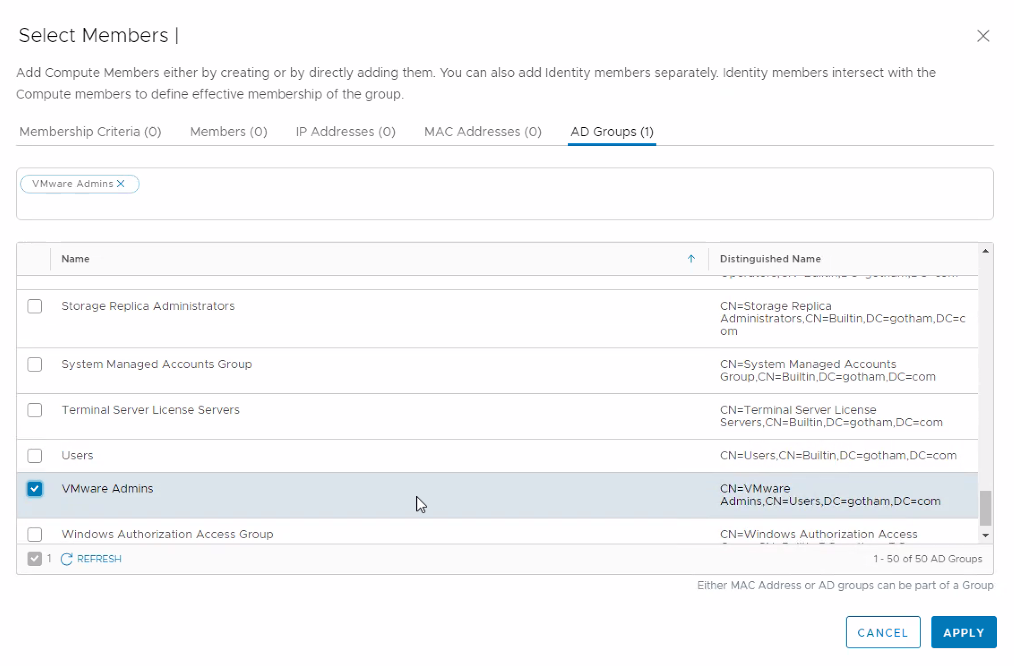
Creating AD groups can be achieved by following the below procedure:
Select Inventory > Groups from the navigation panel.
Click Add Group.
Enter a group name.
Click Set Members.
Click AD Groups to add Active Directory Groups.
Click Apply and then Save.
Adding Rules
When adding dFW rule, general principles should be followed.
dFW was covered in part 1 of the series:
IDFW Scaling
I’ve been looking into IDFW for a while and one of the things I can’t find too much literature on is the scalability of the solution, in terms of best practice.
VMware does a terrific job of providing configuration maximums but I wanted to discuss the platform itself.
What size NSX Managers should be used?
What resources should be present on the AD Server(s)?
There is no guideline for this and I think it’s for a reason because it varies from environment to environment. Small environments would likely get away with medium size NSX Manager appliances. But when do we scale to large appliances? My recommendation would be to monitor the NSX Appliances and the AD Server(s) and scale vertically or horizontally as appropriate. If you can deploy large NSx Managers from the start, then it helps, but they should still be monitored. The sizing of each component is something you and your customers need to work out on a case by case basis.
I’m working with IDFW more as of late. I’ll look to revisit this section and update it with my experiences of when and why I had to scale the NSX Managers and/or the AD servers.
Automate using Terraform
Unfortunately, I don’t believe the Terraform provider has the ability to configure the IDFW. However, if I’m mistaken, please point me in the right direction and I’ll update the post.
I do however think it will be available soon, with NSX-T 3.1.1 having “NSX Policy API support for Identity Firewall configuration”. I hope to see an update in the NSX provider in the coming weeks/months. Rest assured, I’ll swing back and update the Automation section.